Ellosoft AWS Credentials Manager CLI Ellosoft Limited
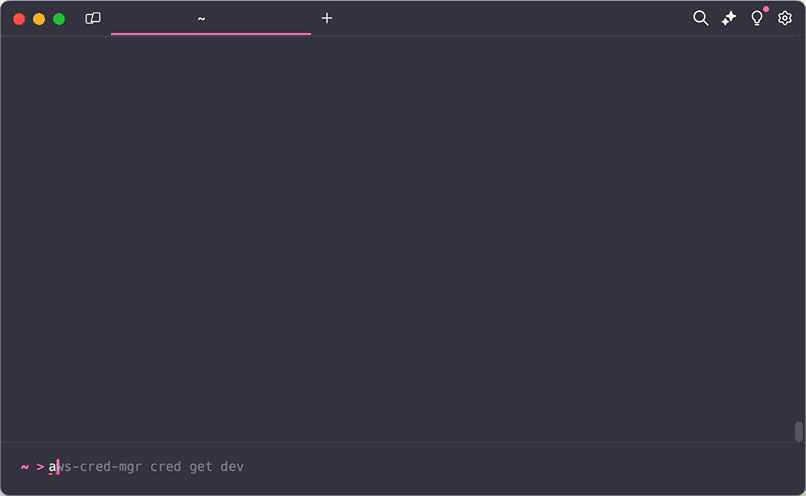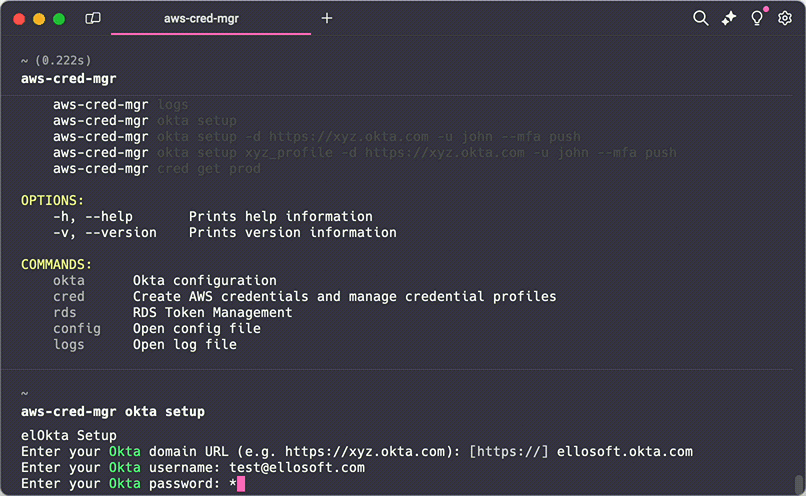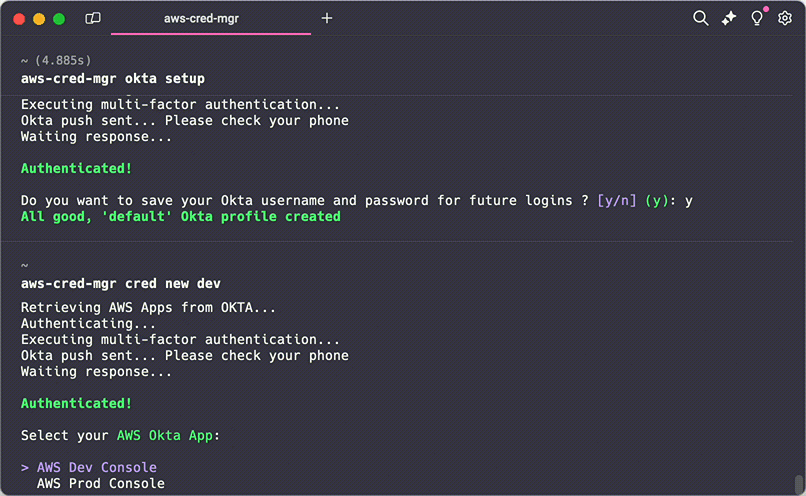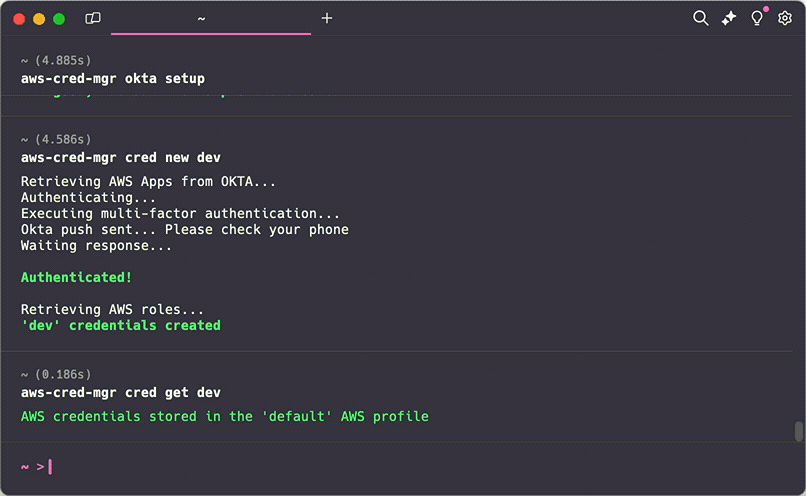
winget install --id=Ellosoft.AWSCredentialsManager -e Ellosoft AWS Credentials Manager CLI is a command-line interface tool designed to simplify managing local AWS credentials, particularly for users employing Okta authentication. It streamlines the process of configuring Okta authentication, creating and managing AWS credential profiles, and handling RDS tokens.
Key Features:
- Okta Authentication Setup: Easily configure Okta authentication with interactive mode or specific domain and username.
- Credential Management: Create, list, and manage AWS credential profiles efficiently.
- RDS Token Management: Securely obtain RDS passwords for databases using straightforward commands.
- Secure Credential Storage: On Windows, credentials are encrypted using DPAPI; on macOS, they're stored with the Keychain API.
- Flexible Configuration: Utilize YAML files to specify variables, templates, and configurations, enhancing customization.
Audience & Benefits: Ideal for developers and DevOps professionals who use AWS and Okta. This tool offers:
- Simplified management of AWS credentials and RDS tokens.
- Secure storage of sensitive information on supported platforms.
- Reduced setup time with interactive configuration options.
- Compliance support through flexible configurations, aiding in meeting organizational security standards.
Installation is straightforward via winget for Windows users, ensuring easy access to enhance your workflow efficiency.